Setting up authentication for Power BI
There are two methods to authenticate. The first method is Interactive mode, which requires user interaction each time a data source is imported. Because of this, import tasks using Interactive mode cannot be scheduled in Dataedo Scheduler. The second method is Service Principal, which uses a client secret from Azure Application Registration and does not require user interaction during import.
When using the Interactive authentication type without Advanced authentication settings, the only prerequisite is that the user you are connecting with has the appropriate permissions. However, when using the Interactive authentication type with Advanced authentication settings or the Service Principal authentication type, you must first have an Azure Application Registration created.
Permissions - all authentication types
User must have at least Viewer access to every workspace and to each object (reports, datasets, dashboards, etc.) they want to document.
You can verify this by visiting app.powerbi.com and checking whether the target workspace and its objects are visible.
Interactive authentication type
In this authentication workflow, we are using user impersonation against Azure Application Registration. In default mode, we are using Dataedo’s Application Registration, but when clicking Advanced authentication settings, it is possible to provide connection details for your own Azure Application Registration.
Required permissions
Metadata is retrieved using the Power BI Admin API. The connecting user must be a Fabric Administrator.
The user must have the following scopes:
Report.Read.AllWorkspace.Read.AllDataset.Read.AllDataflow.Read.AllDashboard.Read.AllTenant.Read.All– required to import usage statistics and perform WorkspaceInfo scans. Microsoft Documentation ›
Interactive authentication using default settings
To use interactive authentication, Authentication Type dropdown should be selected to Interactive and Advanced authentication settings checkbox should be unchecked.
- Power BI
- SharePoint Lists
- Azure Data Factory
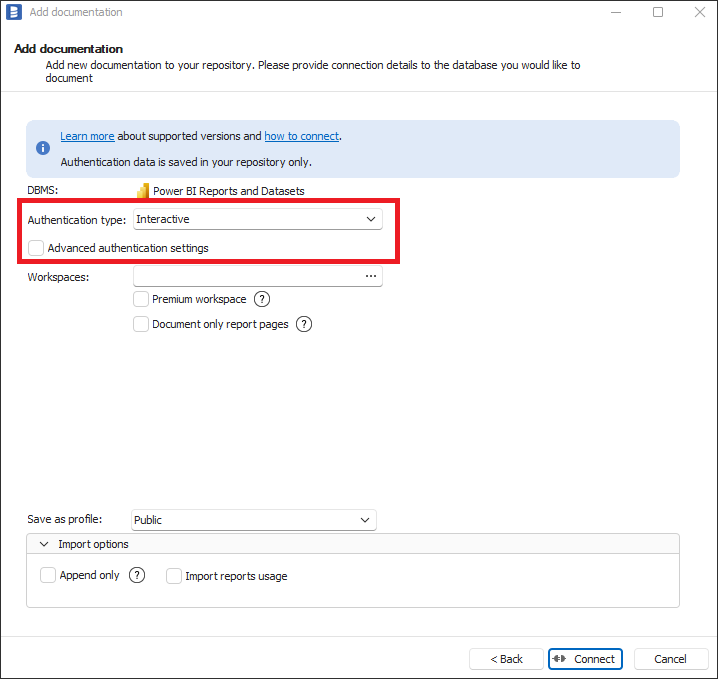
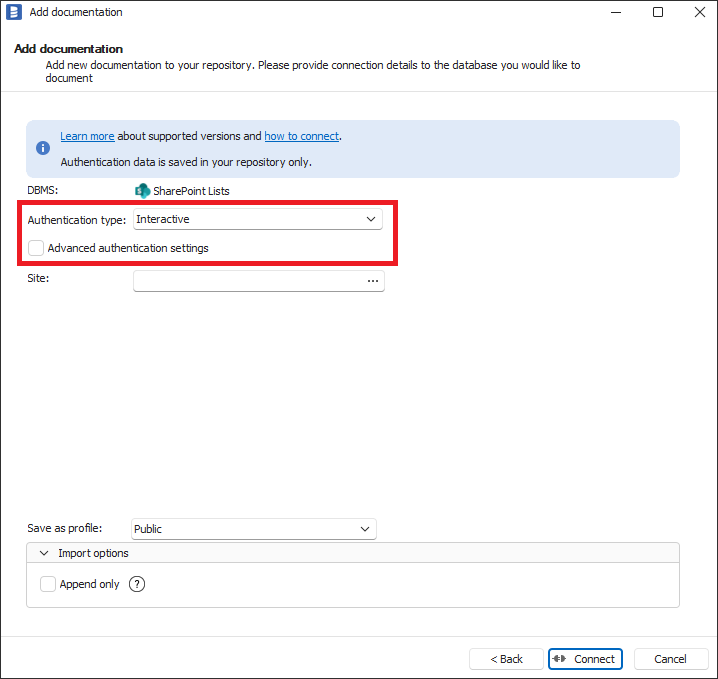
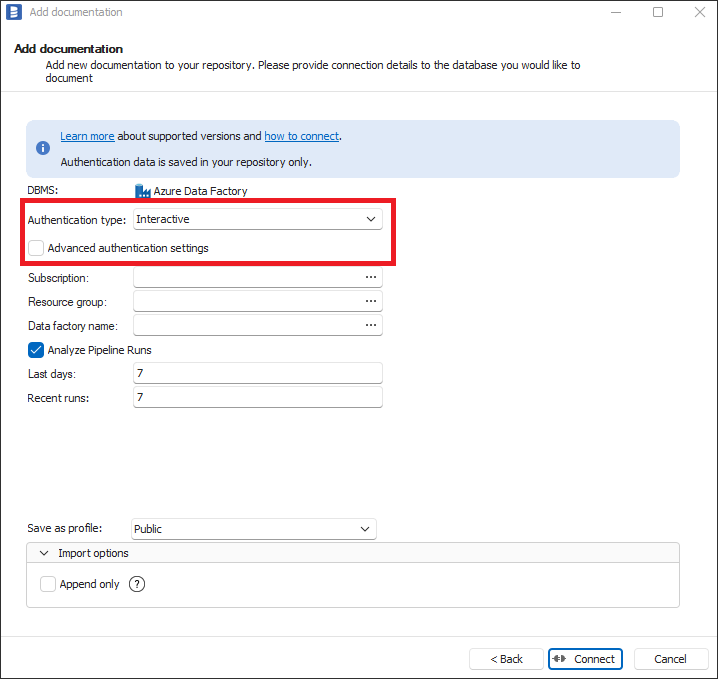
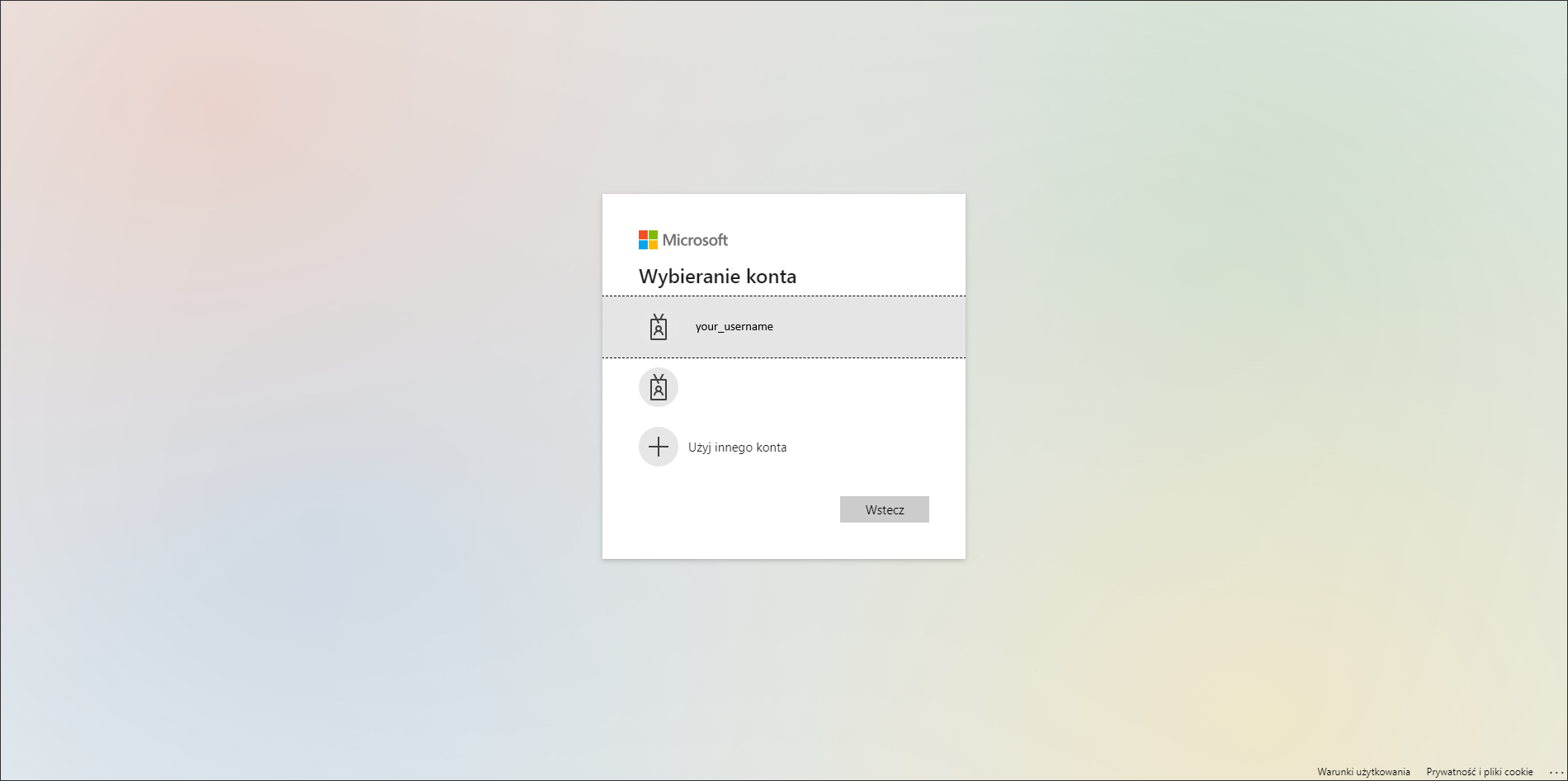
When you click Connect or select some details (workspace), your default browser will be opened with Microsoft login screen. After successful login, you can close the browser and start import. In some cases, for the first time use there will be Azure Administrator consent required and there will be Administrator action needed as explained in Adding Azure Administrator consent to Azure Application Registration section below.
Interactive authentication using advanced authentication settings
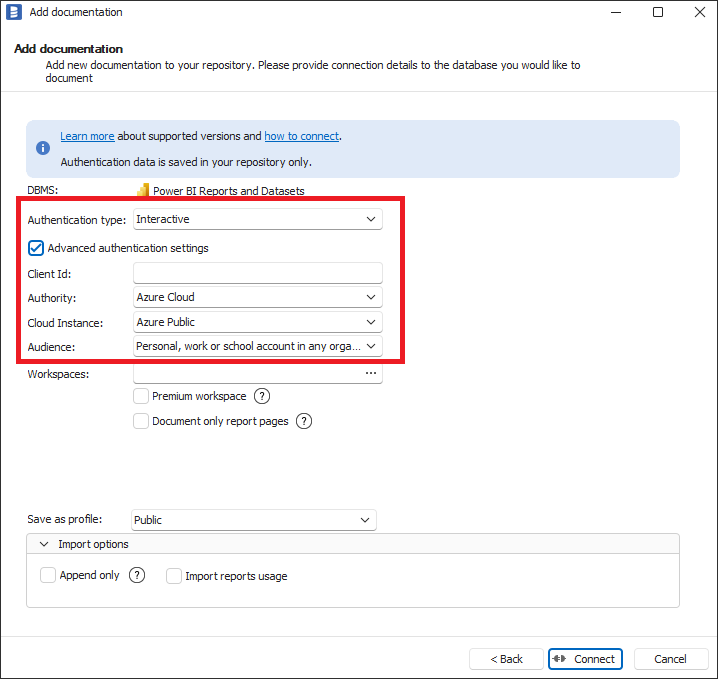
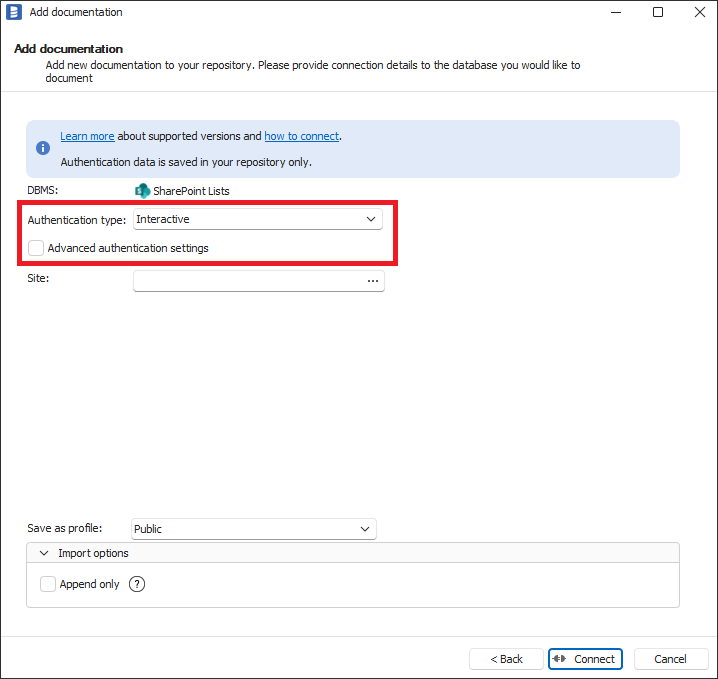
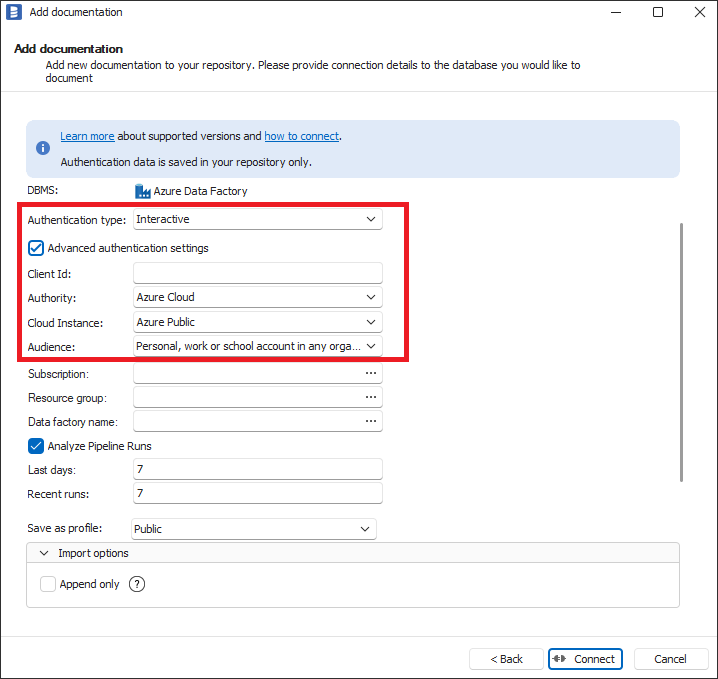
To use interactive authentication using advanced authentication settings. Authentication Type dropdown should be selected to Interactive and Advanced authentication settings checkbox should be checked. Then please enter your Application Registration Client Id to Client Id textbox. How to create Azure Application Registration and where is Application Registration Client Id is explained in Creating Azure Application Registration section below. When you are using not default settings in Application Registration or Azure Cloud Instance other than Azure Public please select proper values in Authority, Cloud Instance and Audience fields.
- Power BI
- SharePoint Lists
- Azure Data Factory
Creating Azure Application Registration
To create an Azure Application Registration:
- Log in to the Azure Portal.
- In the search bar, search for App registrations and select it from the list.
- From the toolbar, on the App registrations page, click + New registration.
- On the Register page for Name, enter a name of your client application, select supported account types, and Redirect URI as Public client/native, with http://localhost redirect URI.
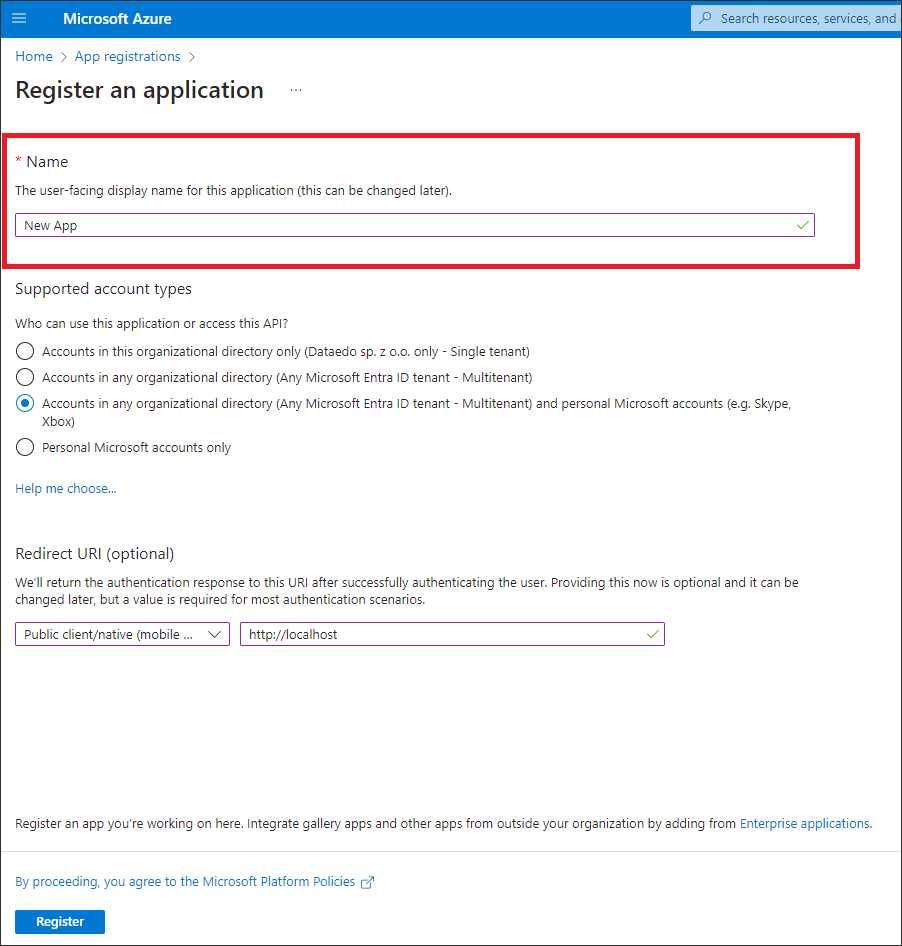
- Click Register.
- On the homepage of your created application, from the Overview screen, copy the values for the Application (client) ID field - this value needs to be pasted into Client Id field in Dataedo.
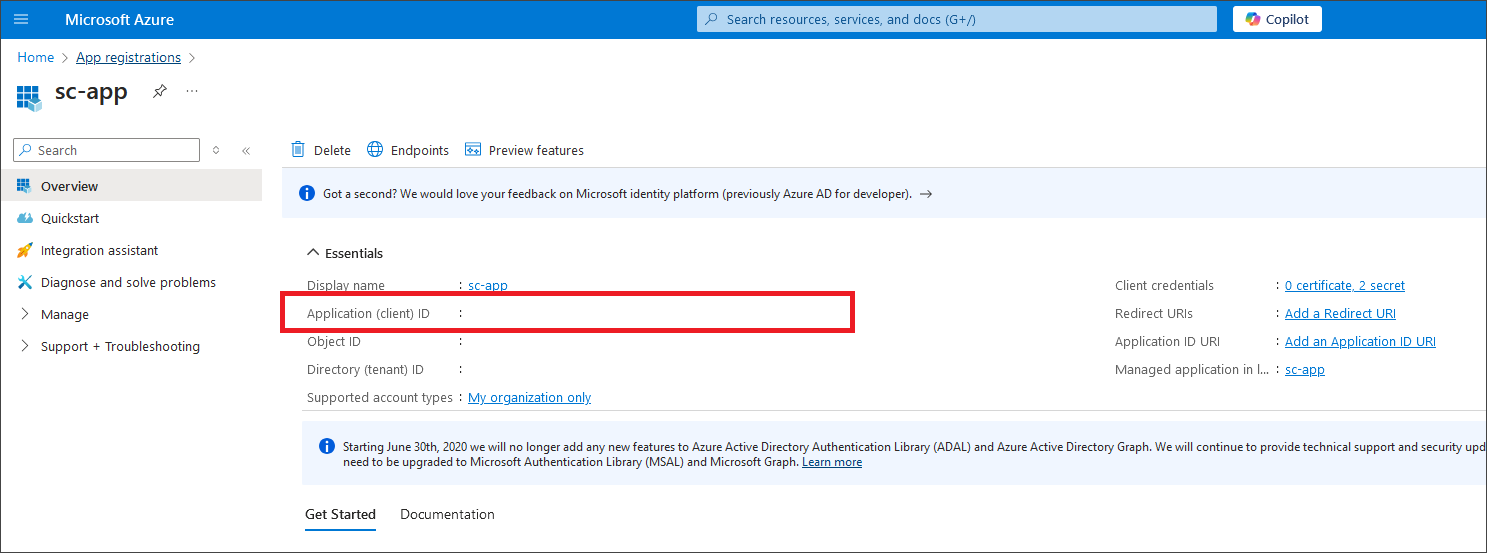
- On the left sidebar of your created application page click on Manage and then click API permissions to assign proper permissions to the application.
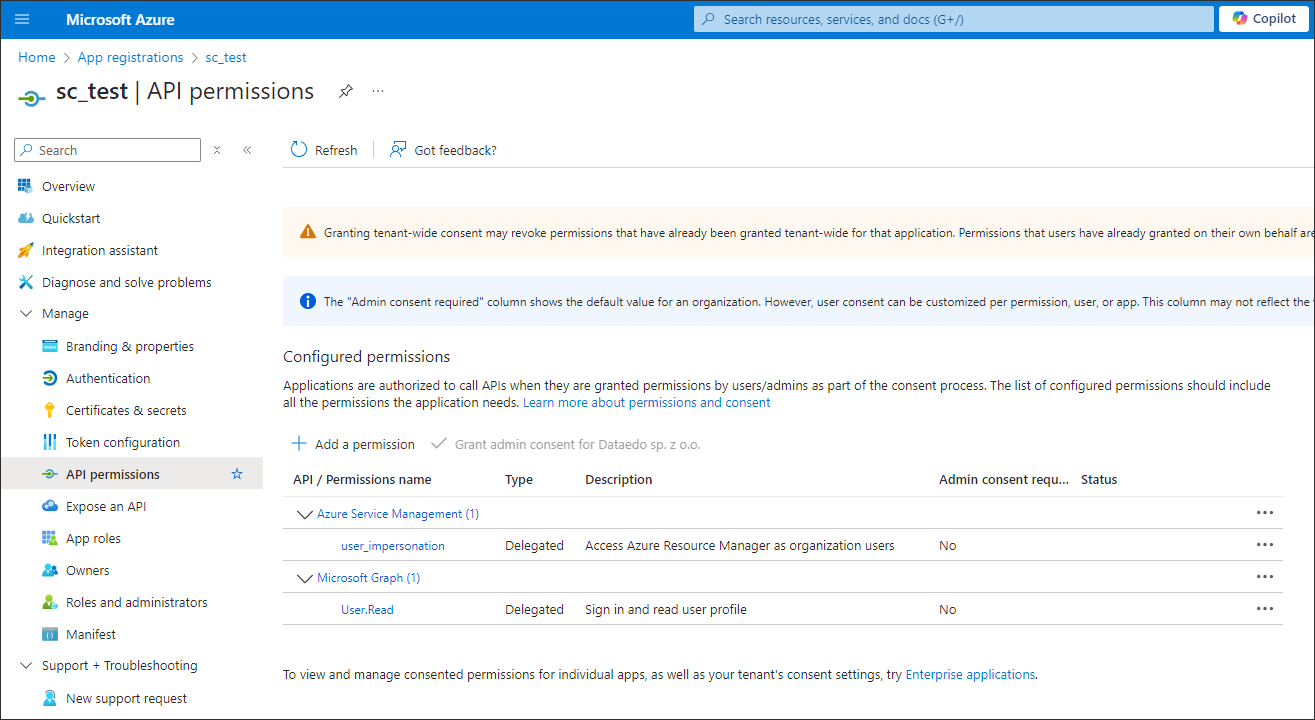
- In API permissions page click Add a permission.
- On the right sidebar Request API permissions click on Azure Services Management.
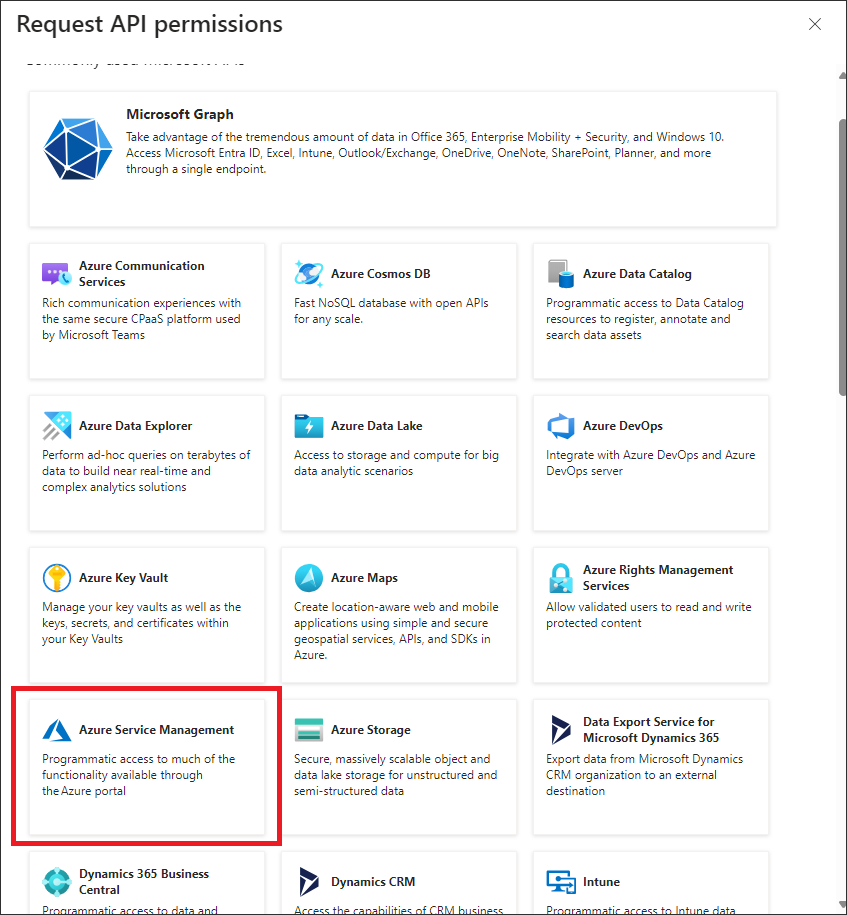
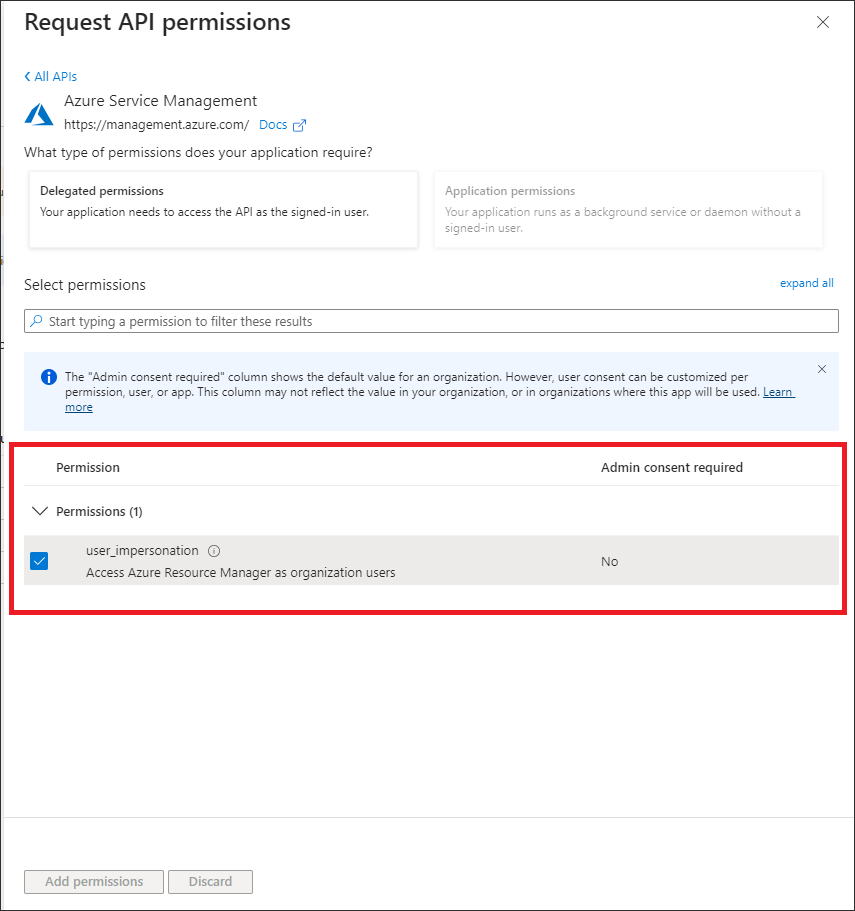
- On the permissions list which will appear after clicking on Azure Service Management check the checkbox user_impersonation and click Add Permissions
Adding Azure Administrator consent to Azure Application Registration
In some Azure subscription configurations, Admin consent may be required for using Application Registration.
If the user encounters a screen like this, it means that requesting Admin consent is disabled for your Azure subscription:

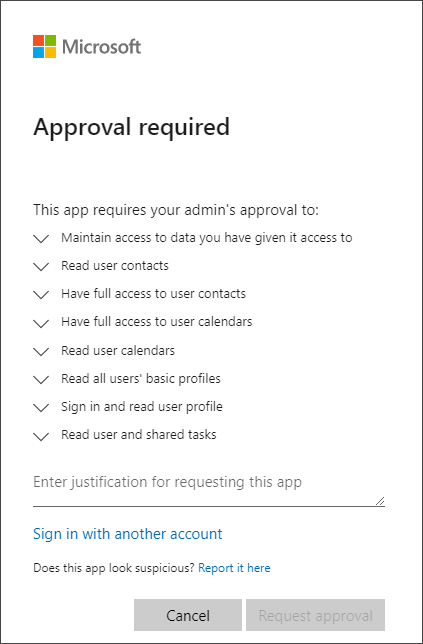
To resolve this, the user needs to see a screen like this, where they can send a request for approval to the Azure Admin:
To enable sending Admin consent requests, the Azure Administrator needs to take the following steps in Azure Portal:
- Open Enterprise applications in the Azure portal.
- In the left sidebar, go to Security and click on the Consent and permissions menu.
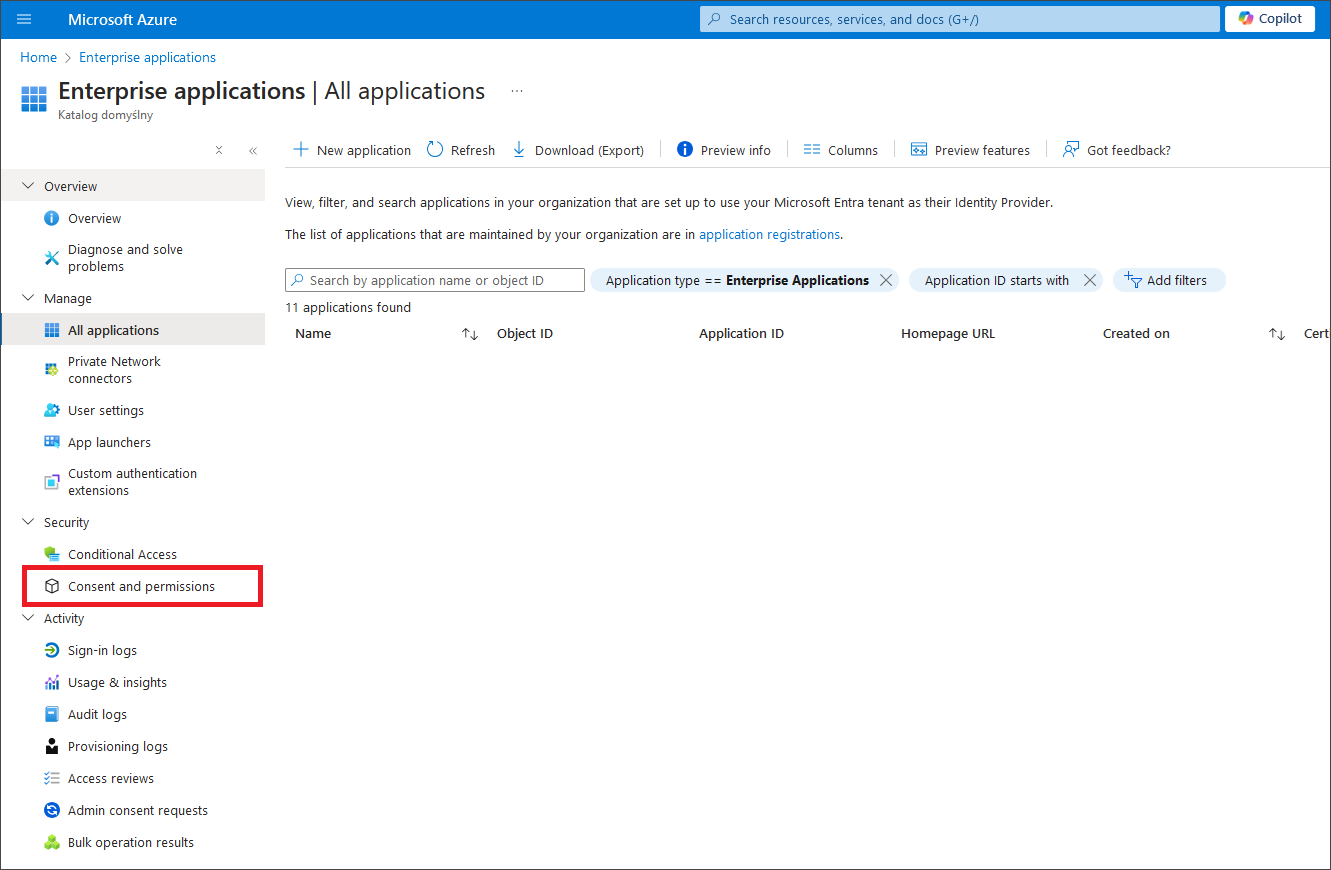
- In Consent and permissions, click Admin consent settings in the left sidebar and select YES for "Admin consent requests – Users can request admin consent to apps they are unable to consent to." Select one or more users, groups, or roles that can consent to applications.
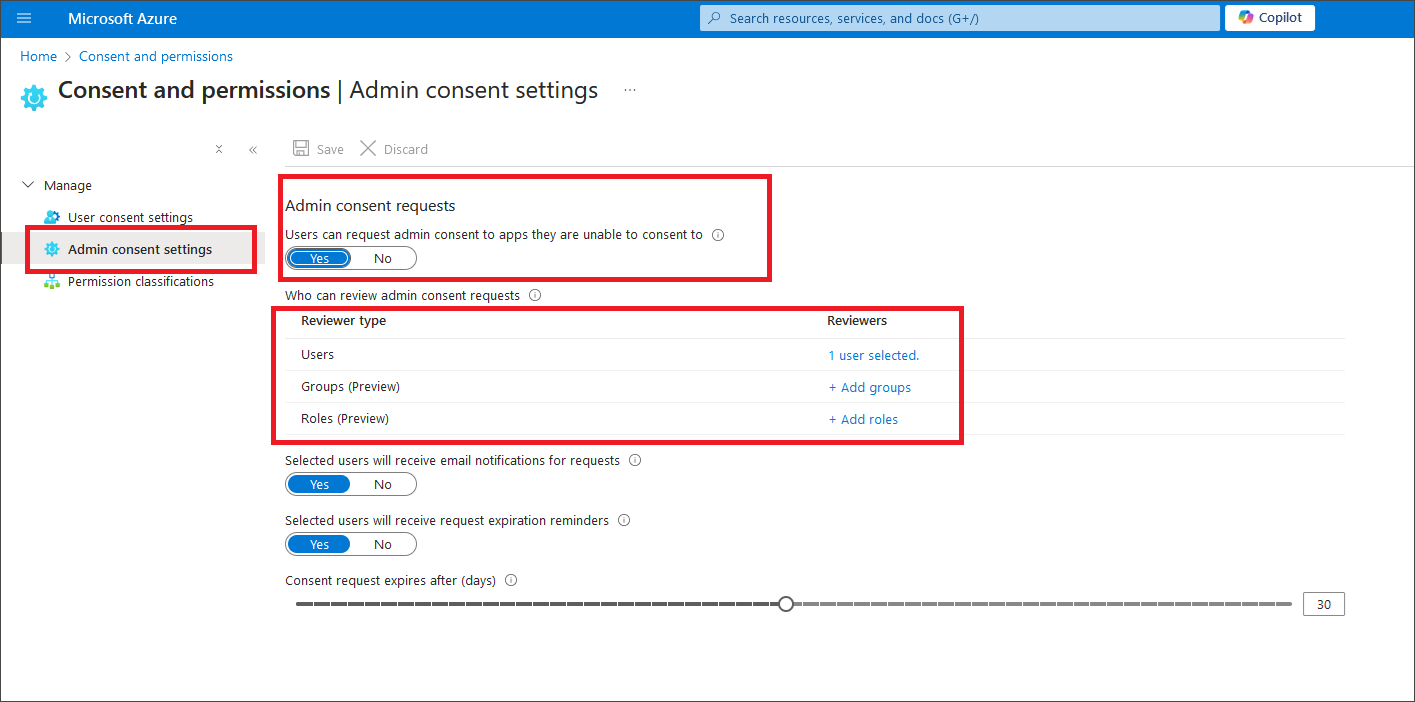
Once consent requests are enabled, the user can send a request for approval:

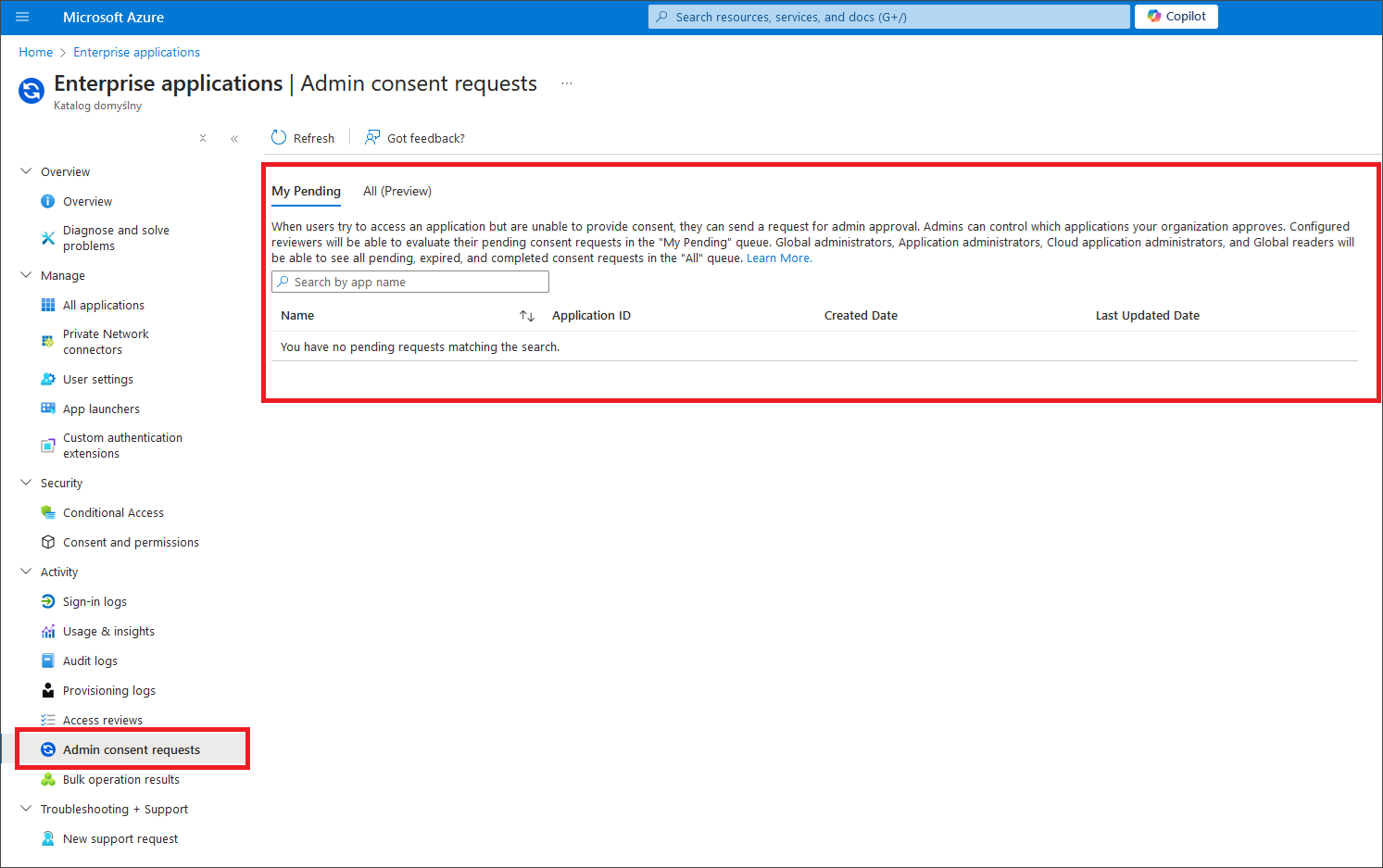
After the request is sent, the Azure Administrator will see the request for review under Enterprise applications in the Azure Portal, within the Activity → Admin consent requests menu. After reviewing and approving the requested permissions, the user will be able to log in and import the Power BI workspace with the Dataedo application.
Service Principal authentication type
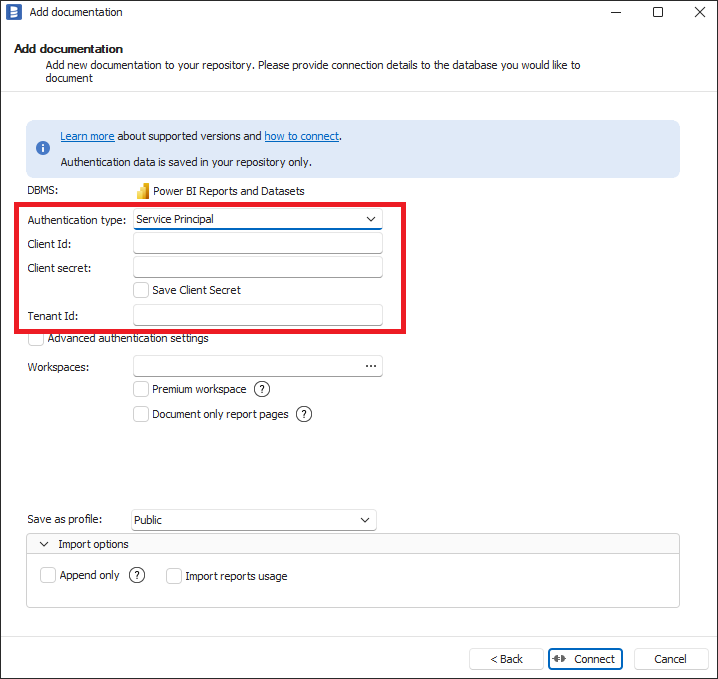
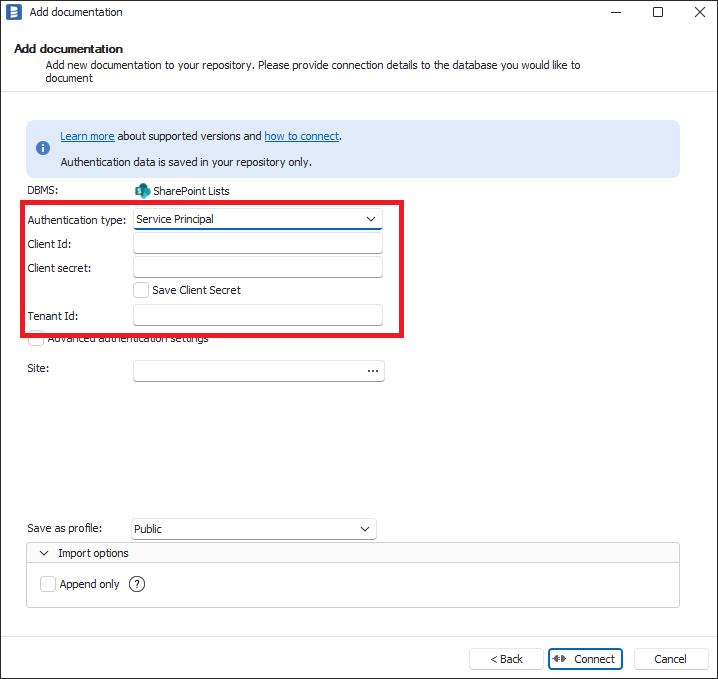
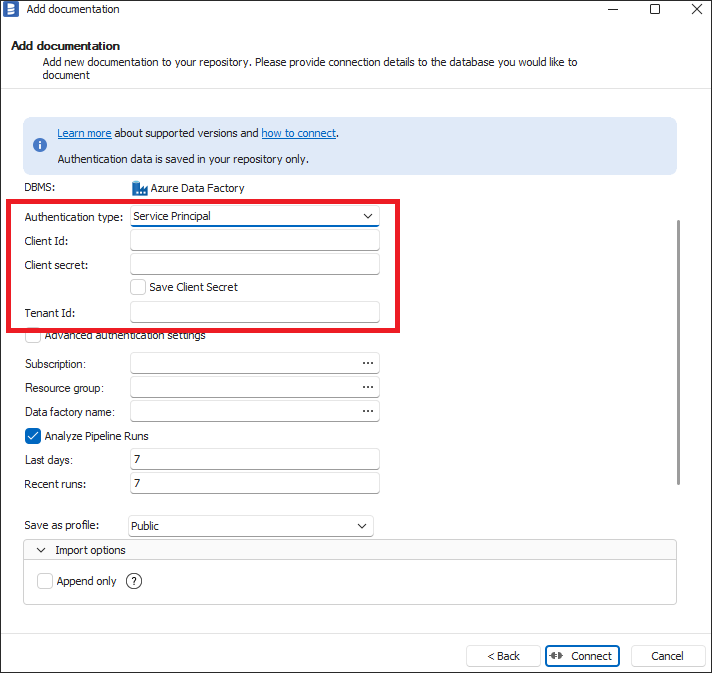
To use the service principal authentication type, please select Service Principal in Authentication Type dropdown and fill Client Id, Client Secret and Tenant Id with proper values from your Azure Application Registration. How to create Azure Application Registration and where those values available are explained in Creating Azure Application Registration section below.
- Power BI
- SharePoint Lists
- Azure Data Factory
Creating Azure Application Registration
To create an Azure Application Registration:
- Log in to the Azure Portal.
- In the search bar, search for App registrations and select it from the list.
- From the toolbar, on the App registrations page, click + New registration.
- On the Register page for Name, enter a name of your client application, select supported account types, and Redirect URI as Public client/native, with http://localhost redirect URI.

- Click Register.
- On the homepage of your created application, from the Overview screen, copy the values for the Application (client) ID field - this value needs to be pasted into Client Id field in Dataedo and Tenant Id into Tenant Id in Dataedo.
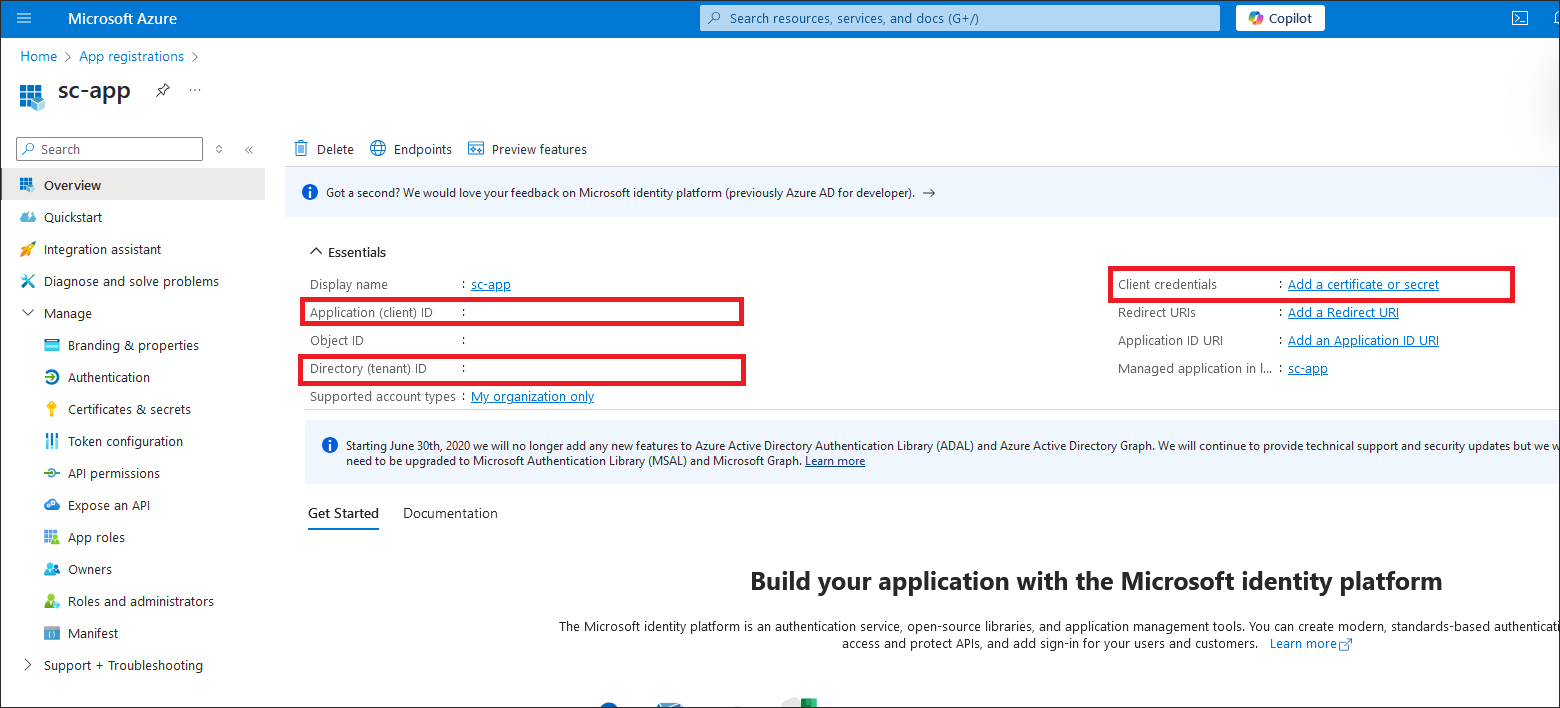
- From the left menu of your created application registration page, click Certificates & secrets.
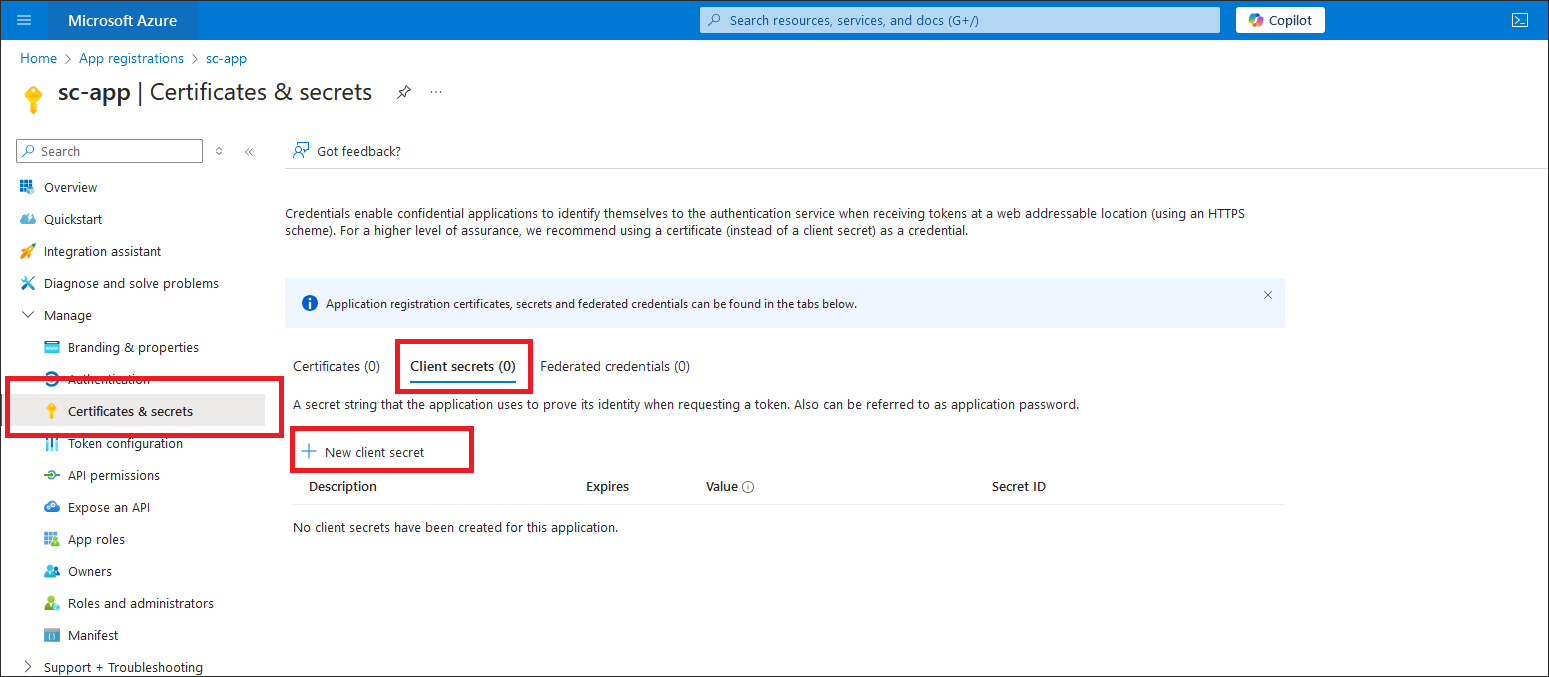
- On the Certificates & secrets page, under Client secrets, click + New client secret.
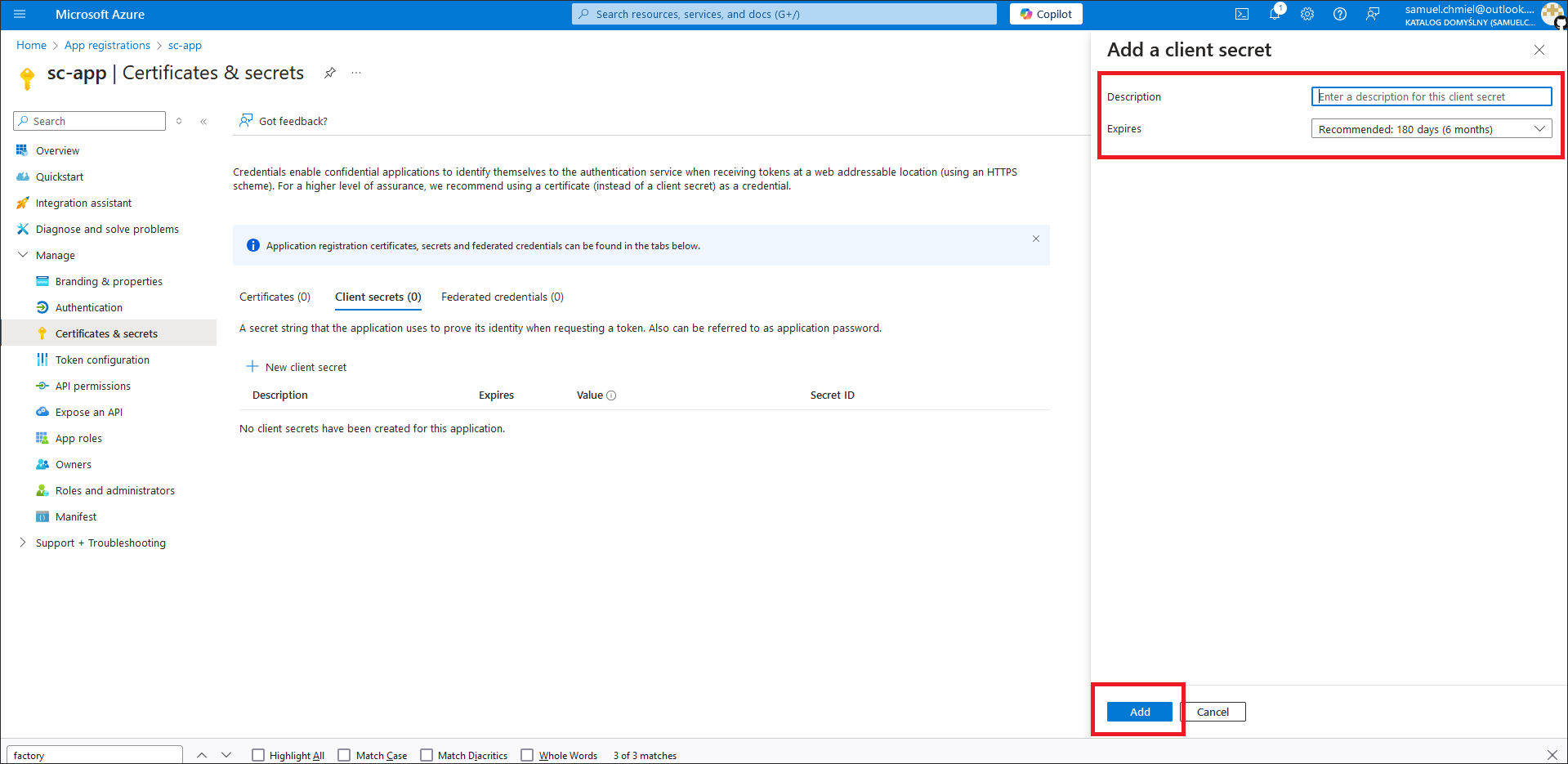
- In the Add client secret screen, enter the description, expiry and click Add
- On the certificates & secrets page, under Client secrets click the clipboard icon to copy it and paste it in Client secret field in Dataedo.
Setting up Service Principal for Power BI
To set up Power BI import using service principal authentication in addition to application registration, it is required to create a security group and assign this group to proper roles in Microsoft Power BI workspace and set up additional settings in Power BI Admin Portal. Each of those steps is explained in Creating security group and Assigning security group and role in Microsoft Power BI below. After setting it up, you are ready to import Power BI using service principal authentication.
If you are using workspaces with Pro license, the user you are connecting with must be a Fabric Administrator otherwise some data may be missing or incomplete . If you are using workspaces with Premium license, this is not required.
Creating a security group
- Login to the Azure Portal.
- In the search bar, enter Microsoft Entra ID and select it from the list.
- In the left menu under Manage section, click Groups.
- Click the New group.
- Set the Group type to Security.
- Enter Group name and description.
- Under Members, click the No members selected link.
- Search for application registration created before and click to select it.
- Click Select.
- Click Create.
Assigning security group and role in Microsoft Power BI
- Open https://app.powerbi.com/home
- Open Workspaces and then select workspace which you wish to import.
- Click Manage Access button.
- Inside the box Enter email addresses enter the name of the security group you created before.
- To generate lineage for dataflows in addition to importing defined parameters for semantic models set it to Member.
- Click Add below the dropdown.
Enable admin API settings in Microsoft Power BI
- Login to https://app.powerbi.com/admin-portal
- From the menu under Admin portal click Tenant settings.
- Under the Developer settings, click Service principals can use Fabric APIs and select Enabled. Under security groups add the security group created before and click Apply.
- Under the Admin API settings, click Allow service principals to use read-only Power BI admin APIs and click Enabled. Under security groups add the security group created before and click Apply.
- Under the Enhance admin APIs responses with detailed metadata click Enabled. Under security groups add the security group created before and click Apply.
- Under the Enhance admin APIs responses with DAX and mashup expressions select Enabled. Under security groups add the security group created before and click Apply.

